|
|
|
|
|
Exercise #2
Blackholes, Sinkholes, and Traceback
Due 11:45PM
(firm)
|
| |
|
In this exercise, you will learn to implement some real ISP techniques, namely a Blackhole, a Sinkhole and Traceback, which are used to deal with DDoS attacks. A Blackhole causes all traffic going to the target to be dropped; a Sinkhole causes all attack traffic to be diverted away from the target; Traceback discovers the ingress points of the attack to your network.
What you will get out of this exercise:
- learn to configure low-level networking on a modern OS,
and on modern router OSs
- a hands-on understanding of how backbone routing in the
Internet works today
- a hands-on experience with real-life ISP techniques to deal with
DDoS attacks
Electronic submissions only.
|
| |
|
Resources
|
|
Read and be familiar with as many of these resources as you can:
|
| |
|
Output
|
|
You will submit a lab report. The lab report should contain
answers to the questions listed in the exercise description. The
lab report should be in ASCII, PostScript, PDF or HTML.
You should name the file ex2.* with the appropriate
file extension. You may prepare the report using any good word
processing software (MS Word, Latex, Lyx).
In addition, you will be asked to submit data files and other
kinds of files. To do this, put your report and all required
files into a directory named ex2. Then tar and gzip
this directory into a file called ex2.tar.gz and
submit it electronically.
(Read the documentation for the Unix "tar" command on how to do this).
Even if you are not able to complete the exercise, be sure to
submit a partial lab report. You will get partial credit for your
efforts.
|
| |
|
Configuring the Topology
|
As before, you will be given the bare, unconfigured topology.
You will need to log on to the routers and the machines and
will configure the topologies.
Setting up the interfaces
You will need to set up an address assignment plan for the
topology.
Setup the first two bytes of all addresses
according to the last four digits of your USC ID.
If your USC ID is
abcdefghij, then all addresses must begin with 1gh.ij. For
example, if your USC ID is xxxxxx1234, then all addresses must be
in the form of 112.34.x.x.
|
| |
|
Steps in the Exercise
|
Remote Blackholing
In this step, you will implement remote blackholing. First, you
will setup the topology shown below and configure routing. Then,
you will use packit to launch attacks from the three attackers
toward the target machine. Finally, you will login to R2 and
propagate a blackhole route, which should reach all the other
routers and stop the attack on the target.
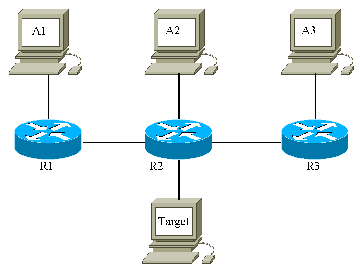
In this topology, R1, R2 and R3 are Cisco routers and the other
machines are Unix workstations.
A1, A2 and A3 are attackers running
packit.
While the experiment is on going, you should also collect
binary
packet traces on the Target using tcpdump without filtering out
any traffic. Read the man page for tcpdump carefully before
embarking on the experiment.
Answer these questions in your lab report.
- Write in your report the address configuration for all
interfaces.
- Run BGP on all routers and configure them in the same
Autonomous System. Figure out how to implement remote blackholing
at the routers. Learn about the Null0 interface, BGP static
routes and the ip next-hop command. Include the running-config of
routers R1, R2 and R3. Call these files r1.blackholing.conf,
r2.blackholing.conf, etc.
- Start a TCP SYN attack. Make sure the source addresses are
randomized. What command options did you use?
- Logon to R2 and issue the appropriate commands to blackhole
the target. What commands did you use? What happens at the
Target?
- Logon to R1, R2, and R3 and issue ping commands to the Target.
List the commands you use and the output. Explain what happens.
- Compress the trace from the Target and include it in your
submission. The trace must be named target.blackholing.trace.gz.
Sinkholing
For this step, you will implement a Sinkhole to divert attack
packets to a sinkhole machine.
Configure the topology shown below.
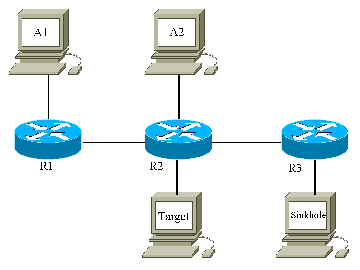
The Sinkhole runs Zebra. As with Part 1, the attackers A1 and A2
will use packit and randomized source addresses.
While the experiment is on going, you should also collect
binary
packet traces on the Target and the Sinkhole using tcpdump
without filtering out any traffic. Read the man page for tcpdump
carefully before embarking on the experiment.
Answer these questions in your lab report.
- Write in your report the address configuration for all
interfaces.
- Include the zebra bgpd files from the Sinkhole. Call the file
sinkhole.sinkholing.bgpd.conf. Also include the running-config of
routers R1, R2 and R3. Call these files r1.sinkholing.conf,
r2.sinkholing.conf, etc.
- Start an ICMP ECHO attack. What command options did you use?
- Issue the appropriate zebra commands at the sinkhole machine
to divert all attack traffic from the target to the sinkhole.
What commands did you use?
- Compress the traces from the Target and the Sinkhole. Include
them in your submission. These traces must be named
target.sinkholing.trace.gz and sinkhole.sinkholing.trace.gz.
Traceback
The final step in the exercise is to trace back the attack
streams at the edge of your network. Remember that in real life,
an ISP may have many links to other networks but only a subset of
them will carry attack traffic for any given attack. In this part
we will combine remote blackholing and sinkholing to implement a
traceback technique that will reveal the ingress interfaces of
the attack. The technique will use a sinkhole to attract a subset
of the ICMP unreachable messages generated by routers after the
target address is blackholed. For this technique to work you need
to configure your sinkhole to advertise a large, unused IP
address space. To find such a space go to the
IANA web page
and pick an appropriate IP range.
Configure the topology as the sinkholing experiment.
While the experiment is on going, you should also collect
binary
packet traces on the Target and the Sinkhole using tcpdump
without filtering out any traffic. Read the man page for tcpdump
carefully before embarking on the experiment.
Answer these questions in your lab report.
- Write in your report the address configuration for all
interfaces.
- Include the zebra bgpd files from the Sinkhole. Call the file
sinkhole.traceback.bgpd.conf. Also include the running-config of
routers R1, R2 and R3. Call these files r1.traceback.conf,
r2.traceback.conf, etc.
- Execute a TCP SYN attack. Write the command line options you
used in your report.
- Figure out how to use a combination of blackholing and
sinkholing, along with the unused address space you picked to
divert ICMP unreachables to your sinkhole. Explain how you did
this in your report.
- Determine the IP address of the interfaces the attack is
coming through. Write those in your report. How did you determine
these addresses?
- Compress the traces from the Target and the Sinkhole. Include
them in your submission. These traces must be named
target.traceback.trace.gz and sinkhole.traceback.trace.gz.
Discussion
Answer the following questions in your lab report.
- Why is Blackholing useful? (1-2 sentences)
- Why is Sinkholing useful? (1-2 sentences)
- Why is Traceback useful? (1-2 sentences)
- Based on your observations, how long would it take to discover
the ingress points of a DDoS attack?
- How easy or difficult are these techniques to implement? Try to
extrapolate on a large network with perhaps thousands of internal
routers and dozens of border routers.
- Are these techniques sufficient to counter DDoS attacks? If no,
explain.
You're done! Submit the report electronically as outlined above.
|
| |
|


